HIPAA Compliance: What Healthcare Providers Need to Know
Understanding and practicing all that is encompassed under HIPAA can be confusing and stressful at times. But as one of the most important legal and ethical guidelines in the industry, it is imperative anyone who has access to patient information understand the law and focus on compliance. Solutions like PaperTracer aid in this effort by offering a secure document repository where only authorized users can access the information that is relevant to their role. In order to clarify some misconceptions or lingering questions, we have created this blog to help guide you through all of the HIPAA standards and provisions.
HIPAA in a nutshell
HIPAA stands for Health Insurance Portability and Accountability Act and was signed into action in 1996 by President Bill Clinton. Its purpose was to modernize the flow of healthcare information in order to ensure the protection of patient medical data. HIPAA does the following things:
- Provides the ability to transfer and continue health insurance coverage for millions of Americans when they change or lose their jobs;
- Reduces healthcare fraud and abuse;
- Requires healthcare organizations to implement secure electronic access to billing, claims, referrals and various other processes;
- Mandates standards for the transmission and handling of patient information.[3]
The act consists of five titles:
- Title I of HIPAA regulates the availability and breadth of health insurance coverage for workers and their families when they change or lose their jobs.[1]
- Title II of HIPAA, known as the Administrative Simplification (AS) provisions, maintains the privacy and security of individually identifiable health information by establishing national standards for electronic health care transactions and national identifiers for providers, health insurance plans, and employers.[2]
- Title III sets guidelines for pre-tax medical spending accounts,
- Title IV sets guidelines for group health plans including coverage of persons with pre-existing conditions, modifies and clarifies continuation of coverage requirements, and
- Title V governs company-owned life insurance policies.
To sum it up, HIPAA is used in order to safeguard patient information and ensure that their personal healthcare data is not being misused, and it is safe from theft or embezzlement.[2]
What is HIPAA Compliance?
There are four groups of guidelines every healthcare provider MUST follow to be HIPAA compliant:
- Privacy Rules
- Security Rules
- Breach Notification Rules
- Enforcement Rules
What is the HIPAA Privacy Rule?
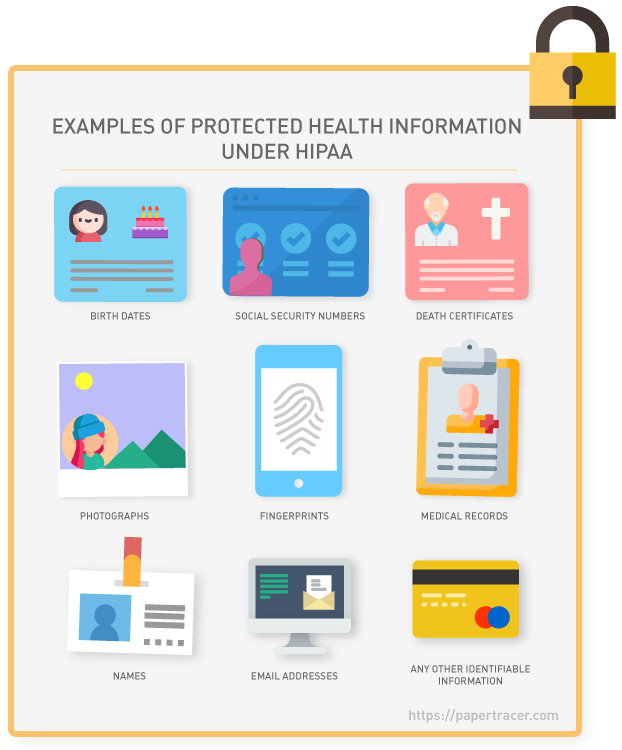
HIPAA privacy rules require medical providers to give individuals access to their PHI including health conditions, treatment plans, notes, images, lab results, and billing information. It also defines how and when healthcare professionals, lawyers, or anyone who can access your PHI can or cannot use that data. This includes past, present, and future conditions, payment for healthcare, and the provision of healthcare to a patient.
The HIPAA Privacy Rule defines PHI as individually “identifiable health information” stored or transmitted by a covered entity or their business associates, in any form or media (electronic, paper, or oral).[1]
What is the HIPAA Security Rule?
The HIPAA Security Rule complements the Privacy Rule by setting the standards required for covered entities to manage electronic PHI (ePHI). The HIPAA Security Rule states, “The Security Rule requires appropriate administrative, physical and technical safeguards to ensure the confidentiality, integrity, and security of electronic protected health information.”[3]
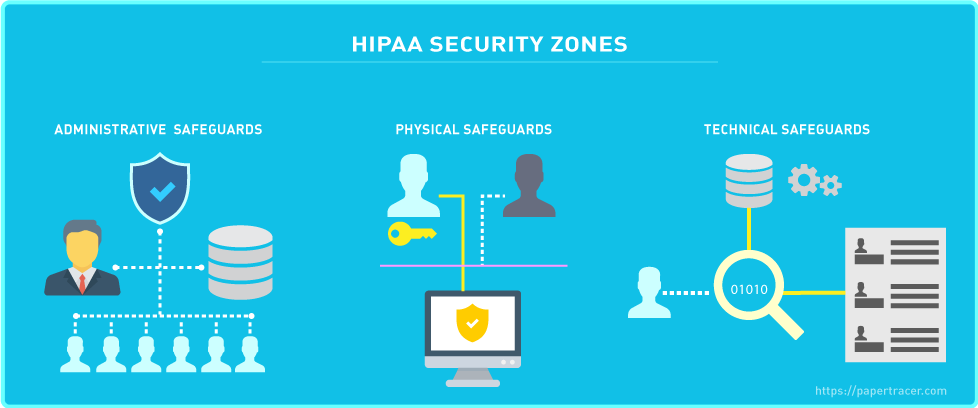
The HIPAA Security Rule is classified into three additional categories with standards, which are explained in detail below:
- Technical Safeguards
Technical Safeguards pertain to the technology which is used to protect ePHI by covered entities. Covered entities are responsible for implementing technical safeguards, which are becoming increasingly more important due to technology advancements in the health care industry. It is important, and therefore required by the Security Rule, for a covered entity to comply with the Technical Safeguard standards and certain implementation specifications.[3]
Standard 1. Access Control
Company personnel should be given a Unique User Identification that can be used to track and monitor system utilization.
Procedures should be implemented to give authorized access to certain employees should an emergency arise.
Machines or software that contain ePHI should have an automated system which logs the user out of the system in the event it sits idle for predetermined time.
Encryption and Decryption strategies should be incorporated into machines that store ePHI.[3]
Standard 2. Audit Controls
Audit Controls should, on a regular basis assess, file and store machine’s usage and ePHI handling. Most information systems provide some level of audit controls with a reporting method, such as audit reports. These controls are useful for recording and examining information system activity, especially when determining if a security violation occurred.
Standard 3. Integrity
The purpose of this standard is to establish and implement policies and procedures for protecting ePHI from being compromised regardless of the source. The integrity of data can be compromised by both technical and non-technical sources. Covered entities should conduct a risk analysis of the integrity of their data, and then implement security measures that will reduce the risks.
Standard 4. Person or Entity Authentication
Individual or Entity Authentication should be set up to guarantee that only approved workers or clients have access to certain information and ePHI. A covered entity may require a password or PIN, require a smart card or key, or require something unique to the individual such as biometric safeguards.
Standard 5. Transmission Security
The Security Rule allows for ePHI to be sent over an electronic open network as long as it is adequately protected. There are two implementation specifications: Integrity Controls, which were already mentioned in Standard 3 and Encryption, where covered entities are required to implement a reasonable and appropriate safeguard to protect transmission of ePHI.[3]
- Physical Safeguards
The Physical Safeguards focus on physical access to ePHI irrespective of its location. ePHI can be stored in a remote data center, in the cloud, or on servers which are located within the premises of the HIPAA covered entity. They also stipulate how workstations and mobile devices should be secured against unauthorized access.[3]
Standard 1. Facility Access Controls
Policies and procedures should be implemented to limit physical access to its electronic information systems and the facility or facilities in which they are housed, while ensuring that properly authorized access is allowed.[3]
Standard 2. Workstation Use
Workstation use policies indicates the utilization and execution of devices and workstations where ePHI is stored. A workstation is defined in the rule as “an electronic computing device, for example, a laptop or desktop computer, or any other device that performs similar functions, and electronic media stored in its immediate environment.”
Standard 3. Workstation Security
Workstation Security involves implementing physical safeguards for all workstations that access electronic protected health information, to restrict access to authorized users. While the Workstation Use standard addresses the policies and procedures for how workstations should be used and protected, the Workstation Security standard to be physically protected from unauthorized users.
Standard 4. Device and Media Controls
The Device and Media Controls standard requires the implementation of policies and procedures that control the receipt and removal of hardware and electronic media that contain ePHI, into and out of a facility, and the movement of these items within the facility.[3]
- Administrative Safeguards
The Administrative Safeguards are the policies and procedures which bring the Privacy Rule and the Security Rule together. They require that a Security Officer and a Privacy Officer be assigned to put the measures in place to protect ePHI, while also overseeing the conduct of the workforce.[3]
Standard 1. Security Management Process
The Security Management Process requires covered entities to implement policies and procedures to prevent, detect, contain and correct security violations. There are four implementation specifications: Risk Analysis, Risk Management, Sanction Policy, and Information System Activity Review. The Sanction Policy requires covered entities to apply appropriate sanctions against workforce members who fail to comply with the security policies and procedures of the covered entity. The Information System Activity Review requires regular review of information system activity, such as audit logs, access reports, and security incident tracking reports. [3]
Standard 2. Assigned Security Responsibility
A security official should be identified and is responsible for routinely screening, creating, and keeping up with the privacy policies and strategies.
Standard 3. Workforce Security
Policies and procedures should be implemented to ensure that all members of the workforce have appropriate access to ePHI, and to prevent those workforce members who do not have access from obtaining access to electronic protected health information.[3]
Standard 4. Security Awareness and Training
Security awareness and training are extremely important as there is no need for the implementation of safeguards if the workforce is not going to adhere to them. Many security risks and vulnerabilities within covered entities are internal. This standard requires covered entities to implement a security awareness and training program for all members of its workforce, including management.[3]
Standard 5. Evaluation System
It is important for a covered entity to know if the security plans and procedures it implements continue to adequately protect its ePHI. To figure out the standing of employees based on their conduct with ePHI, an evaluation system should be in place. Policies and procedures should be routinely monitored and evaluated.[3]

What is the HIPAA Breach Notification Rule?
The HIPAA Breach Notification Rule requires covered entities to notify an individual of improper access to their PHI within 60 days. Also, even if ransomware encrypts ePHI, it is still considered a breach and falls under this rule. If more than 500 PHI records are impacted, you must notify the Department of Health and Human Services (which in turn gets the OCR involved) – and you’re required to issue a press release about the breach.[4]
What are Enforcement Rules?
The Enforcement rule establishes rules governing the compliance responsibilities of covered entities with respect to cooperation in the enforcement process. Individuals or companies report HIPAA violations to the Office for Civil Rights (OCR), and the OCR is responsible for investigating and reviewing those violations. The Enforcement rule governs the process and grounds for establishing the fine amount of a civil penalty and establishes rules governing the procedures for hearings and appeals where the covered entity challenges a violation determination.[4]
Covered entities should be aware of the following penalties:
- A violation attributable to ignorance can attract a fine of $100 – $50,000.
- A violation which occurred despite reasonable vigilance can attract a fine of $1,000 – $50,000.
- A violation due to willful neglect which is corrected within thirty days will attract a fine of between $10,000 and $50,000.
- A violation due to willful neglect which is not corrected within thirty days will attract the maximum fine of $50,000.
Fines are imposed per violation category and reflect the number of records exposed in a breach, risk posed by the exposure of that data and the level of negligence involved. Penalties can easily reach the maximum fine of $1,500,000 per year, per violation category. In addition, the penalties for willful neglect can also lead to criminal charges being filed. Victims of a breach can also file Civil lawsuits for damages. The organizations most commonly subject to enforcement action are private medical practices, hospitals, outpatient facilities such as pain clinics or rehabilitation centers, insurance groups, and pharmacies.[6]
The most common disclosures to the HHS are:
- Misuse and unauthorized disclosures of patient records.
- No protection in place for patient records.
- Patients unable to access their patient records.
- Using or disclosing to third parties more than the minimum necessary protected health information
- No administrative or technological safeguards for electronic protected health information.[6]
What is a HIPAA Violation?
There are several ways to violate HIPAA’s requirements. The most common violations are due to negligence or incomplete compliance that results in a data breach of PHI or unauthorized release or access by unauthorized employees to PHI. HIPAA violations can continue for many months, or even years, before they are discovered. The longer they persist, the greater the penalty will be when they are eventually discovered. It is therefore important for HIPAA-covered entities to conduct regular HIPAA compliance reviews to make sure HIPAA violations are discovered and corrected before they are identified by regulators.[4]
There are three main ways that HIPAA violations are discovered:
- Investigations into a data breach by OCR (or state attorneys general)
- Investigations into complaints about covered entities and business associates
- HIPAA compliance audits
Even when a data breach does not involve a HIPAA violation, or a complaint proves to be unfounded, OCR may uncover unrelated HIPAA violations that could warrant a financial penalty.[5]
What is a Covered Entity?
A covered entity is a health care provider, a health plan or a health care clearing house who, in its normal activities, has any access to PHI. However, there are exceptions. The hospital is the covered entity and responsible for implementing and enforcing HIPAA-complaint policies, but most healthcare providers employed by a hospital are not covered entities.[6]
What is a Business Associate?
A “business associate” is a person or business that performs certain functions or activities that involve the use or disclosure of PHI on behalf of, or provides services to, a covered entity. Examples of Business Associates include lawyers, accountants, IT contractors, billing companies, cloud storage services, email encryption services, etc. Before gaining access to PHI, the Business Associate must sign a Business Associate Agreement with the Covered Entity stating what PHI they can access, how it is to be used, and that it will be returned or destroyed once the task it is needed for is completed. While the PHI is in the Business Associate´s possession, the Business Associate has the same HIPAA compliance obligations as a Covered Entity.[6]
HIPAA Risk Assessment – What should it consist of?
Throughout the HIPAA regulations, there is a lack of guidance about what a HIPAA risk assessment should consist of. The Department of Health and Human Services stipulates that the goal of a HIPAA risk assessment is for a Business Associate to proactively conduct an internal review of their company and to identify potential vulnerabilities, threats and risks to the PHI that their company receives, transmits or maintains. Here are some objectives of a HIPAA risk assessment:
- Identify the PHI that your organization creates, receives, stores and transmits – including PHI shared with consultants, vendors and Business Associates.
- Identify the human, natural and environmental threats to the integrity of PHI – human threats including those which are both intentional and unintentional.
- Assess what measures are in place to protect against threats to the integrity of PHI, and the likelihood of a “reasonably anticipated” breach occurring.
- Determine the potential impact of a PHI breach and assign each potential occurrence a risk level based on the average of the assigned likelihood and impact levels.
- Document the findings and implement measures, procedures and policies where necessary to tick the boxes on the HIPAA compliance checklist and ensure HIPAA compliance.[6]
HIPAA compliance isn’t just about understanding and obeying the law – it’s about maintaining a trusting relationship with your customers through the protection of their data. Compliance with HIPAA is an ongoing exercise, not just a one-time test. It is crucial that Covered Entities and Business Associates remain vigilant in their endeavors to understand and practice all that is encompassed within HIPAA. If you are concerned or unsure about any element of HIPAA, it is recommended to seek professional advice. As previously discussed, ignorance of HIPAA is not an excuse and does absolve a company or person of noncompliance. The time and resources to fully understand, implement and maintain HIPAA guidelines are considerable, but the cost of a violation could be catastrophic.
Sources:
[1] https://www.hipaaguide.net/hipaa-for-dummies/
[2] https://www.cms.gov/Regulations-and-Guidance/Administrative-Simplification/HIPAA-ACA/index.html
[3] https://outsquaremd.com/hipaa-compliance-checklist-for-2019/
[4] https://www.varonis.com/blog/hipaa-compliance/
[5] https://www.hipaajournal.com/common-hipaa-violations/
[6] https://www.hipaajournal.com/hipaa-compliance-checklist/
